Part 2 — Config File Management
This is part 2 of a continued series on how to configure Jenkins on a Kubernetes cluster. The goal of the series is to have a fully functioning continues integration and delivery Jenkins up and running. Part 1 described how to install Jenkins and the necessary plugins and how to configure them for Kubernetes. This part will describe the necessary configuration files that are going to be used in the pipeline.
Config File Management
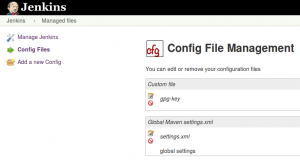
We need two files for a Maven release. The gpg-key that will be used to sign the deployment artifacts and the settings.xml for server Ids, deployment URLs and Jenkins user names and passwords.
gpg-key
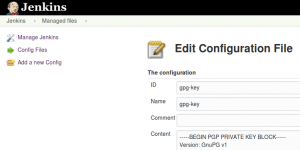
- ID: gpg-key
- Name: gpg-key
- Content: — – BEGIN PGP PRIVATE KEY BLOCK — – …
The private key will be used to sign deployment artifacts via maven. We are going to use the maven-gpg-plugin plugin. The keyname must be set to the name of the gpg-key. The Jenkins Docker image that we are using will start a gpg daemon and is going to use the provided gpg-key and the provided gpg private passphrase to sign artifacts automatically.
[xml title=“pom.xml” firstline=“1”]
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-gpg-plugin</artifactId>
<configuration>
<keyname>ANRI Software</keyname>
</configuration>
<executions>
<execution>
<id>sign-artifacts</id>
<phase>verify</phase>
<goals>
<goal>sign</goal>
</goals>
</execution>
</executions>
</plugin>
[/xml]
maven-settings-global
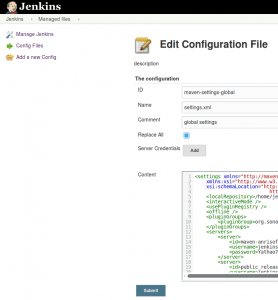
- ID: maven-settings-global
- Name: settings.xml
- Comment: global settings
- [x] Replace All
- Content: <settings xmlns=“http://maven.apache.org/SETTINGS/1.0.0” …
Example settings.xml
We are not going to use Server Credentials. If we use Server Credentials then all servers that are manually added in the <servers> block are going to be replaced by those Credentials, but we need at least one special server configuration: the site-ssh. There we must configure the SSH ports to access the Docker Container where we are going to send our generated site pages. via scp.
There are additional configurations that will work only with our Jenkins Docker image. We are going to use scp to copy HTML pages to a Docker Nginx Image. The Docker Nginx Image is going to be deployed as a container on our Kubernetes cloud and will provide the generated mvn site:site HTML pages. I was thinking in using WebDAV to transfer files to the Nginx web server, but for that I had to implement an authentication and user management. SSH already provides authentication and I can safely use the Jenkins SSH key to transfer the HTML pages.
We are also adding SonarQube host URL and login token. That will be used by the maven sonar:sonar goal. This configuration is taken from the official documentation: Analyzing with SonarQube Scanner for Maven
[xml title=“settings.xml” firstline=“9”]
<pluginGroups>
<pluginGroup>org.sonarsource.scanner.maven</pluginGroup>
</pluginGroups>
…
<profile>
<id>sonar</id>
<activation>
<activeByDefault>true</activeByDefault>
</activation>
<properties>
<sonar.host.url>https://sonarqube.anrisoftware.com</sonar.host.url>
<sonar.login>xxxx</sonar.login>
</properties>
</profile>
[/xml]
